Securing Python applications: preventing vulnerabilities


Powering everything from dynamic web applications to revolutionary mobile applications, programming languages like Python have become pillars of modern digital infrastructure. However, this exponential growth comes with a crucial responsibility: to ensure the security of these applications against constantly evolving cyber threats.
By neglecting safety, the developers expose user data and systems to significant risks, such as Theft of information, the malicious intrusions And the reputational damage. To mitigate these risks, it is crucial to take a proactive approach to security right from the start of the development process.
Let's dive into this comprehensive guide to securing Python applications together.

I. The main vulnerabilities of Python applications
A. Injection vulnerabilities
- Cross-Site Scripting (XSS) : Allows an attacker to inject malicious JavaScript code into a web page that can steal cookies, redirect users to malicious sites, or perform unauthorized actions.
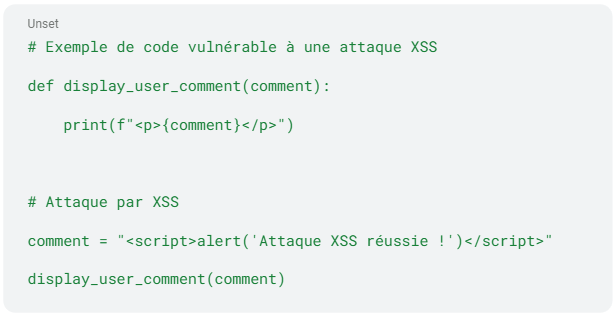
B. Authentication and authorization breaches
- Weak passwords : Using passwords that are easy to guess, such as birth dates or common words, makes user accounts vulnerable to brute-force or form-filling attacks.
- Insecure session management : Session tokens that are weak, predictable, or stored insecurely can allow attackers to hijack legitimate users' sessions and access their data.
C. Data validation and disinfection issues
- Incorrect data entry : The lack of thorough validation of user input can allow attackers to inject malicious code, falsify data, or bypass security protections.
- Insecure data storage : Storing sensitive data, such as passwords or financial information, in plain text or using weak hashing algorithms exposes them to leaks and hacks.
D. Deficiencies in error handling and logging
- Unhandled errors : Unmanaged errors can reveal sensitive information to attackers, such as call stack traces or detailed error messages, making it easy to exploit flaws.
- Insufficient logging : Lack of security event logging or inadequate logging can mask suspicious activity and make it difficult to identify and resolve incidents.
E. Use of outdated or insecure libraries and dependencies
- Known vulnerabilities : The use of libraries or dependencies known to have security flaws exposes the application to targeted attacks and facilitates the exploitation of vulnerabilities.
- Missing updates : Not applying library and dependency security updates leaves the application vulnerable to new threats and discovered flaws.
By understanding the types of common vulnerabilities and adopting appropriate protection measures, Python developers can create applications that are more secure and resistant to attacks.

II. Best practices for securing Python applications
A. Adopting a secure coding approach
For the Python developers, it is crucial to follow established safety guidelines, such as theOWASP Python Security Cheat Sheet. These methodologies make it possible to prioritize security right from the design of the application. By incorporating these practices early in development, Application developers can reduce the risk of vulnerabilities.
B. Employ threat modeling
The Python developer job requires identifying potential threats to the application. For this, a needs analysis being safe is essential. Then, put in place effective measures to mitigate the risks identified.
C. Use static code analysis tools
Les IT developers should use static code analysis tools to detect and correct common coding errors. These tools also make it possible to identify potential security breaches, thus ensuring that Web applications are sturdy and secure.
D. Implement robust entry validation and disinfection mechanisms
Validating all user input is an essential practice for Web developers. This ensures that the data received is as expected and disinfected to remove any malicious code or character, increasing the security of user interfaces.
E. Use robust authentication and authorization techniques
To ensure application security, Full stack developers should store passwords securely using hashing and salting techniques. In addition, implementing role-based access control makes it possible to limit user privileges, an essential practice for web projects.
F. Handle errors properly and log events
Managing errors centrally helps prevent sensitive information from being leaked. In addition, logging relevant security events makes it easy to analyze incidents, a critical task for everything application developer.
G. Keeping libraries and dependencies up to date
It is essential for Professional developers to regularly apply security updates in order to correct known vulnerabilities. Using libraries and dependencies from trusted sources is also essential to ensure the security of software solutions.
H. Adopting secure network deployment and configuration practices
Deploying applications in secure environments and configuring web servers to protect applications from common attacks are essential practices for mobile application developers And the computer designers developers. This ensures that the computer applications are protected against threats and remain functional.

III. Advanced security techniques for Python applications
A. Leveraging web application frameworks for built-in security features
Les web application developers can take advantage of the security features built into popular frameworks suchlike Django and Flask. These frameworks offer protections such as the prevention of CSRF and XSS attacks, and make it easier to manage authentications And permissions secure. By exploiting these tools, developers can improve the safety of Web applications that they design.
B. Implement encryption techniques for sensitive data
For the Python developers, it is essential to encrypt confidential data at rest and in transit using encryption algorithms strong and secure encryption keys. This includes securing databases and network communications of mobile applications and Web. For example, the backend developers can use libraries suchlike PyCrypto or Cryptography to implement these techniques effectively.
C. Using code obfuscation to protect intellectual property
To protect the intellectual property, the computer developers can make code more difficult for attackers to understand and analyze through obfuscation. This technique is particularly useful for software developers And the programmers working on business applications Or software solutions innovative. By making the code less readable, professional developers protect their secrets and proprietary algorithms against competition and malicious threats.
D. Conduct regular security audits and penetration tests
Les application developers should conduct regular security audits and penetration tests to identify remaining vulnerabilities and configuration flaws. These audits allow integrative developers And to programmer-analysts to verify the effectiveness of the security measures put in place. They should include unit tests and functional tests to ensure complete coverage of potential risks.
E. Stay up to date on emerging threats and vulnerabilities
To maintain the safety of computer applications, the Python developers should follow the safety advisories and updates of libraries and frameworks that they use. La Technology watch is essential for updating security practices in line with new threats. By collaborating with web agencies and by participating in trainings and certifications Continue, the developers can stay up to date with the latest security advancements.
By applying these advanced security techniques, application developers ensure the protection of mobile applications, Web, and software solutions that they create, while meeting the requirements of the developer profession In the computer science field.
Conclusion:
By following the best practices described in this guide, Python developers can create secure and reliable applications that protect user data and maintain trust in their products and services. Application security is an ongoing process that requires constant vigilance, adaptation, and collaboration between developers and security teams. By taking the necessary steps to secure their applications, Python developers can contribute to a safer and more reliable digital world.
Are you looking for a new challenge?
Discover our latest job offers on our Talents website.
To deepen your knowledge of this exciting profession, dive into the articles in our Blog.
Together, let's take your career to new heights!
Spontaneous application
Are there currently no offers that match your profile? Share your spontaneous application with us!


.jpeg)

